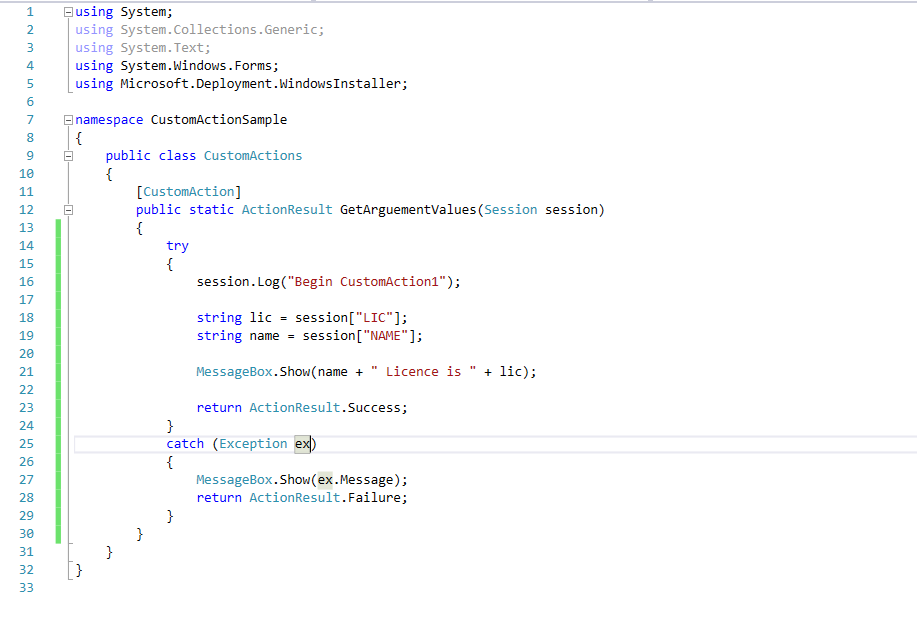
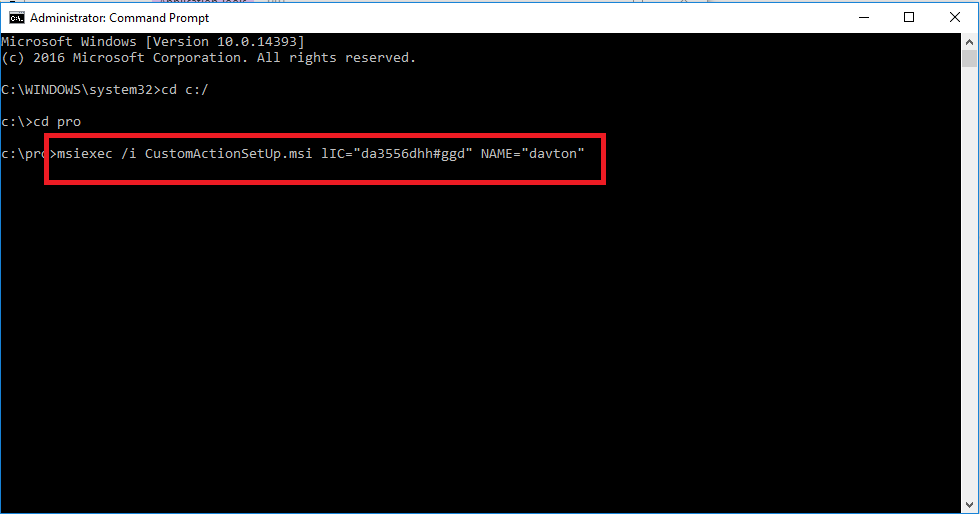
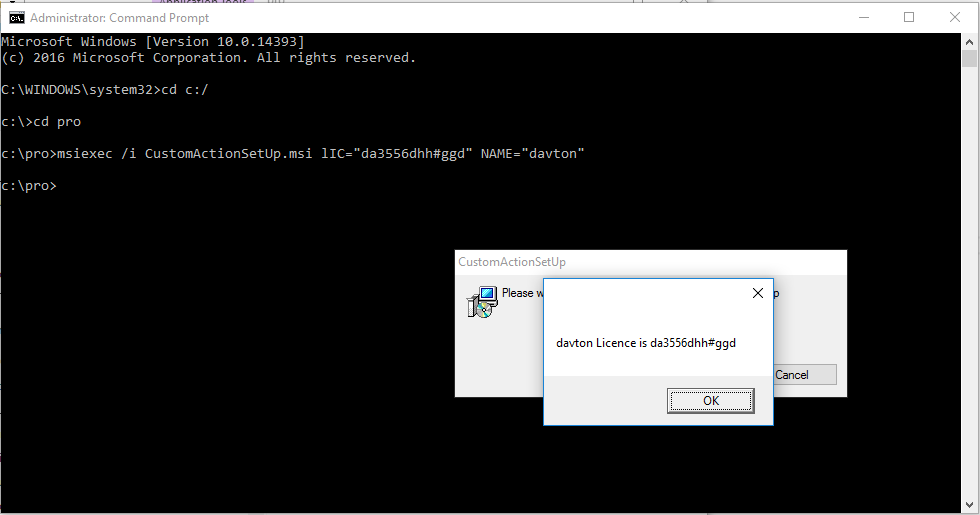
Davton have implemented a number of different authentication mechanisms as part of our work integrating SAAS applications with Outlook and Office 365, including oAuth, oAuth2, single sign on using federated Active Directory, and simple username and password. Recently we were asked by a customer to use a third party service called Auth0 which provides ‘authentication services’ as a service.
This article describes how we used Auth0 authentication with an Outlook plugin. (Note: Davton is not affiliated with Auth0 in any way)
Why do we need Auth0?
Davton integrates SAAS applications with Outlook. In this case, the Outlook plugin would upload to the SAAS application, the email address of the sender of specific emails. This information is communicated via an API – and the API requires a protocol to allow the Outlook plugin to be authenticated. One option would be to build in a username/password mechanism into the SAAS application. An easier solution is to allow the user to be authenticated by a third party application. That application is Auth0.
What is Auth0?
Auth0 is a third party (freemium) service which abstracts how users authenticate to applications or to systems. Developers can use the Auth0 authentication service for any programming language and on any stack to authenticate users to connect with the application. There are several methods that developers can use to connect users to the application using Auth0. They include.
- Social network logins: Google, Facebook, Twitter, and any OAuth2, OAuth1 or OpenID Connect provider.
- Custom credentials: username + passwords
- Passwordless systems: Touch ID, one time codes on SMS, or email
- Enterprise directories: LDAP, Google Apps, Office 365, ADFS, AD, SAML-P, WS-Federation, etc.
Figure 1 shows the mechanism of how Auth0 connects users with the applications.
Auth0 provides Software Developers Kits (SDKs) for all major platforms such as .Net, PHP, Python, Java, NodeJS, android, IOS etc. It’s very simple and easy to create the integration to authenticate users to connect with applications using Auth0.
Auth0 Account
Before we begin development, it is necessary to create an account on the Auth0 service to use Auth0 authentication.We will need the details of this account later.
Creating a sample Outlook plugin which integrated with Auth0
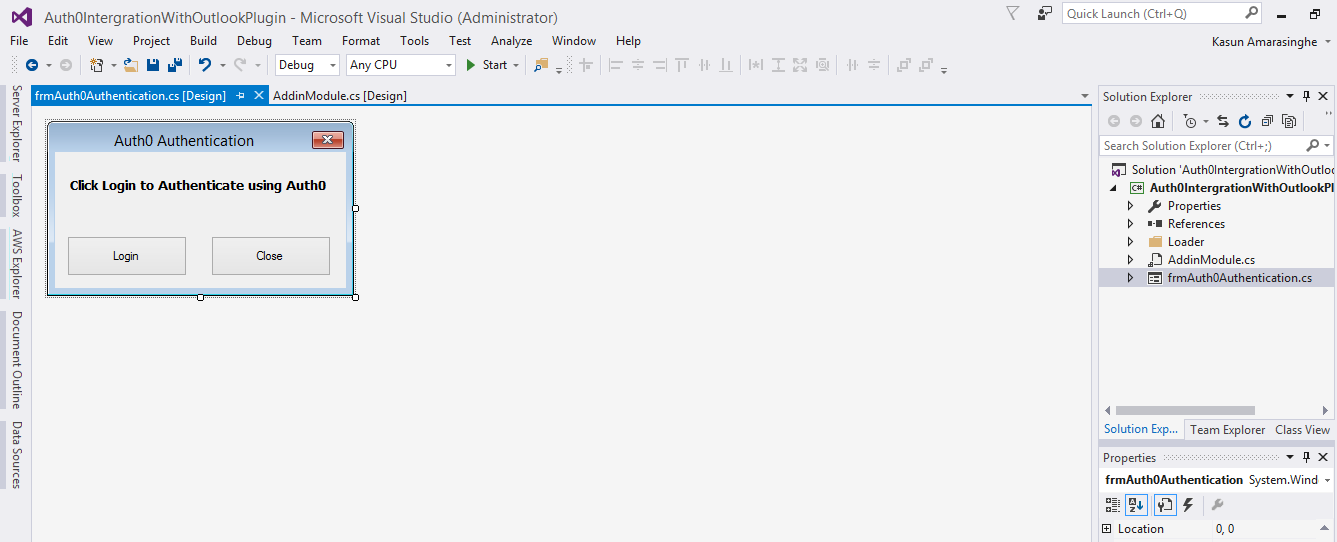
This article describes how to integrate Auth0 in an Outlook plugin by creating a sample Add-in for Outlook. The details of how to create the add-in are beyond the scope of this article, so we will start from the point of creating a windows form which is displayed when we want the user to logon to the service.
Below we can see the Windows form which has been created to allow the user to login.
Adding Auth0 assembly for windows forms to the plugin project
After creating the windows form design we need to add the Auth0 assembly to the plugin project to create the Login button functionality.
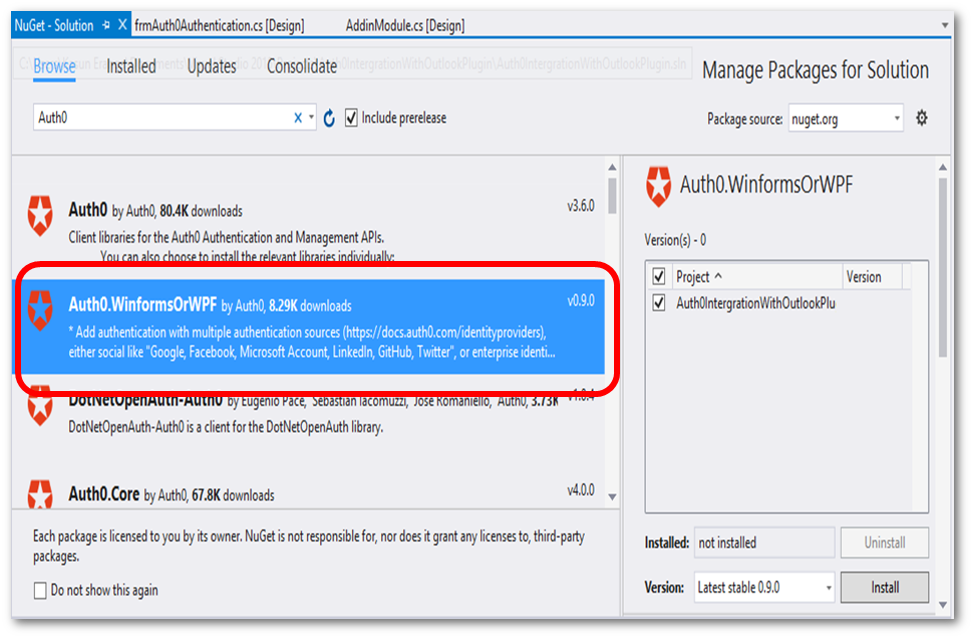
Go to “Tools > NuGet Package Manager” and click “Manage NuGet Packages for Solution”. Then click on Browse and type “Auth0” in the search text box and select “Auth0.WinformsOrWPF” from the list of assemblies in search results (figure 8).
Install the assembly to the sample project.
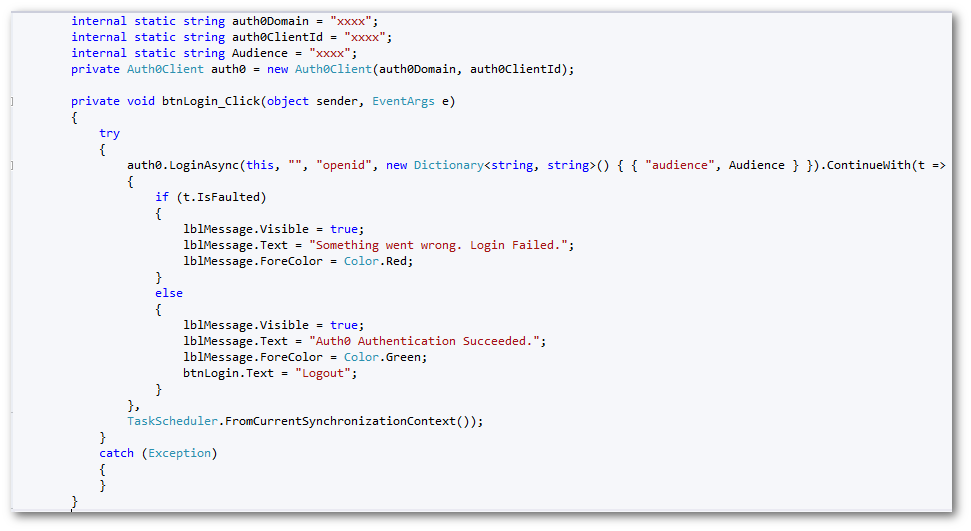
After that double click on the Login button to add the functions to the Login button. – The picture below shows the code snippet for the Login button functionality which was given by Auth0.
You can find further details on the auth0 web site here: https://auth0.com/docs/quickstart/native/wpf-winforms
Strongly-named key
At this stage you will need to refer to the account information for your Auth0 account. The auth0Domain and auth0ClientId will be required in our code.
Important: Auth0.WinformsOrWPF requires a strongly-named key. Without a strong key for this assembly Outlook will fire an exception when we click on the ribbon button we created.
Please refer to “https://blog.devoworx.net/2014/03/13/signing-a-strong-key-to-an-existing-dll-that-you-dont-have-the-source-to-it/” for more information on how to sign a strongly-named key for Auth0.WinformsOrWPF assembly.
Add the Auth0.WinformsOrWPF assembly reference to the sample project after signing a strongly-named key for Auth0.WinformsOrWPF assembly.
Running the sample Outlook Plugin
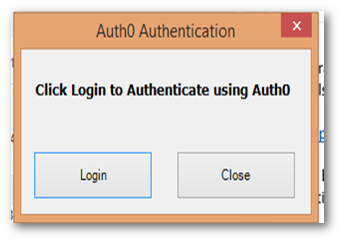
When we compile and run our sample plugin, at the appropriate point, the plugin will display our windows form with the login request.
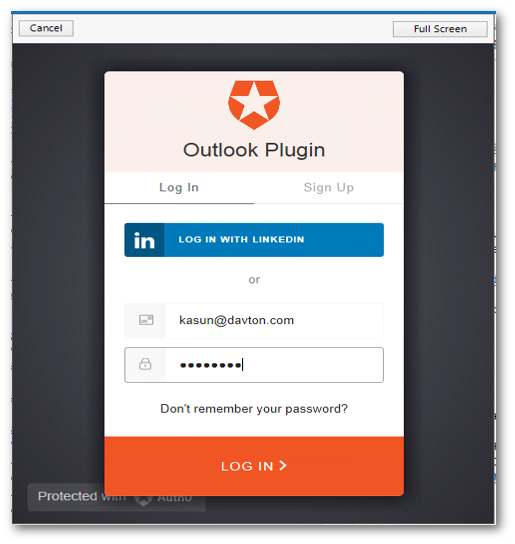
Now we can click on the Login button to authenticate using Auth0 login form as follows.
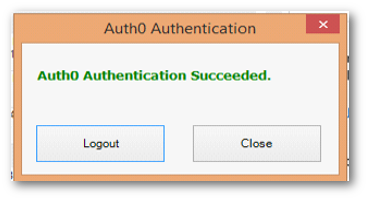
We can either login using our username and password or we can sign up and then can login to the application using Auth0 authentication. Also we can login using our LinkedIn profile login too. All the validations are done in this authentication form of Auth0. We don’t need to do validations by ourselves. So if we logged in successfully we can see the following message in our windows form as follows.
Summary
So using these steps we can use Auth0 authentication for our Outlook plugin. One of the most important things is to sign a strongly-named key for Auth0.WinformsOrWPF assembly, otherwise we can’t implement Auth0 authentication in Outlook.
Finally I hope this article will be helpful for the developers who implement Outlook plugins using Auth0 authentication.
Written by Kasun Amarasinghe May 2017